It’s always refreshing when hacking is just funny and not new threatening APT attacks or huge data breaches.
Lately I stumbled upon this tweet:
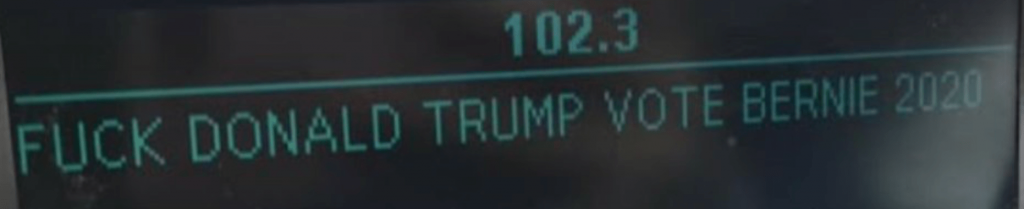
After a nice laugh, I was curious to understand how this works.
And most importantly if it can happen.
First of all, it’s important to understand how this information is broadcasted to then know what are the possible vulnerabilities.
The protocol responsible for broadcast such information is called RDS
RDS is a method to transmit information such as station name, song title, alternative frequencies, etc. from the radio station to the listener.
Jonti (Jonathan Olds) from Wellington New Zealand wrote an informative and elegant article that will explain to you how this works. Also he created JMPX a software-based FM stereo encoder with RDS support.
Once you understand how RDS works, then it’s time to know how it can be hacked. And I couldn’t find more fun and engaging presentation than Injecting RDS-TMC Traffic Information Signals by two guys Andrea Barisani Chief Security Engineer and Daniele Bianco Hardware Hacker.
The video is both hilarious and informative, it’s a must watch.
Also, you can check the full presentation.

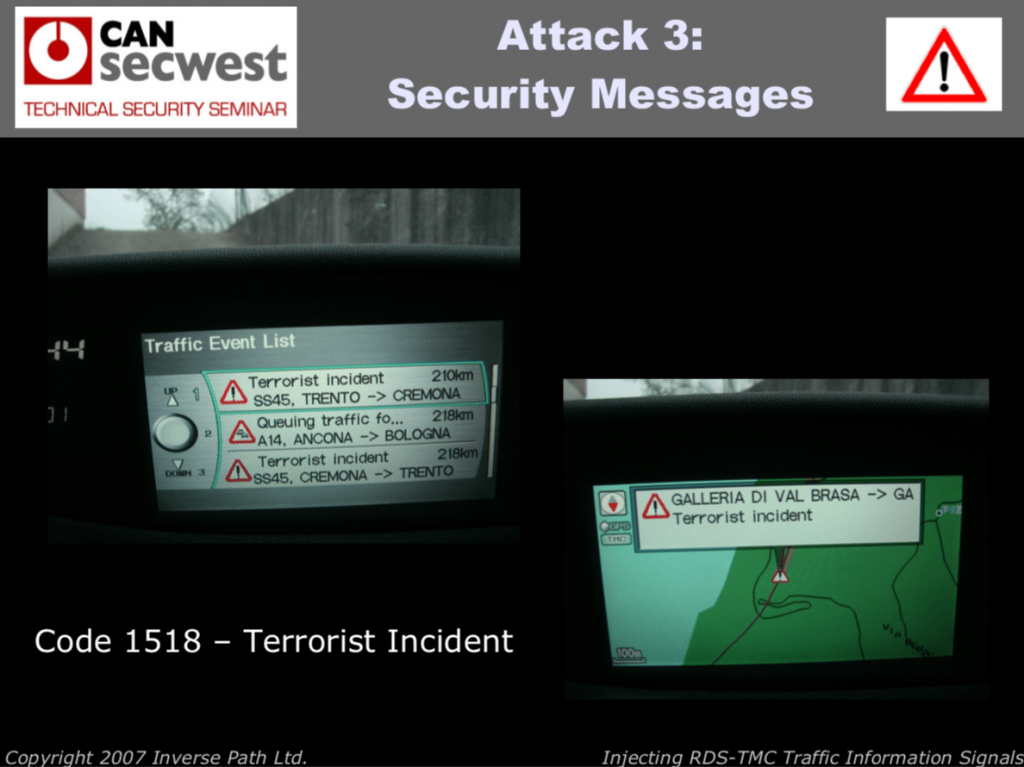
Just some examples of their sense of humor and fun Hack.
Fake radios are nothing new as during WWII they were vital in disseminating disinformation between enemy lines.

A transcript from the fake radio German Freedom Station.
You can find more here.
Now add to fake radios, RDS to havea new dimension of disinformation.
This is a valid reminder that It’s always good to question two times the information that we receive.
Stay vigilant!



 .
.